Our security awareness and training content is highly adaptive customized to meet your needs. That being said, we base much of our content on guidance from the SANS Institute, NIST (National Institute of Standards and Technology), and ENISA (European Network and Information Security Agency).
Our training approach follows recognized standards and guidelines from the NIST Cybersecurity Framework and SP800 publications to “aid an organization in expressing its management of cybersecurity risk by organizing information, enabling risk management decisions, addressing threats, and improving by learning from previous activities.”
Security awareness training should be the process of educating people about:
-
- the risks and vulnerabilities facing their business environment
- the tools they can use to minimize these risks and vulnerabilities
- the mechanisms a company has in place by which people are able to keep their knowledge current.
Furthermore, it should reduce risk through creating:
-
- Awareness of confidentiality, availability, and integrity risks that face the business
- Awareness of vulnerabilities that affect computing systems with which users interact
- Knowledge of corporate policies and procedures designed to address these risks
- Understanding of roles and responsibilities
To be successful, we believe that security awareness training needs to be relevant, effective and entertaining, not dull, boring and mandatory. This should be a mixture of formal and informal training, delivered in multi-mode delivery formats to keep participants engaged, and with key themes presented and reinforced by ongoing awareness reminders to make learning permanent.
Furthermore we encourage a differentiated approach for various groups of users, such that in a hospital environment for example, nursing and support staff receive different training from that of physicians, which is different again from IT staff who usually have elevated access privileges and therefore may pose greater risk.
Some staff groups may need to meet very basic learning objectives on key themes to build foundational understanding, whereas other groups may need concise to-the-point instruction supported by business justification and reason. Highly privileged users may need to be reminded of their responsibilities and the need to consistently follow policies, procedures, standards and guidelines.
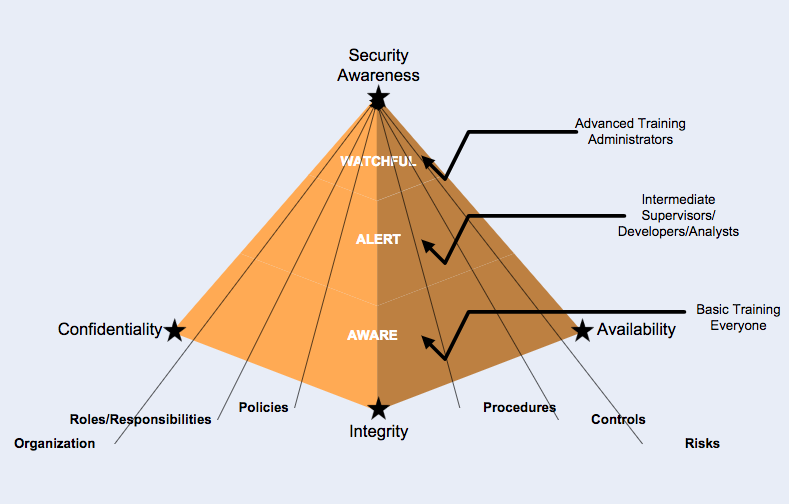
Through a gradual process of targeted awareness themes, user security awareness can be improved over time in order to reduce risks of spear phishing / social engineering, and other common attacks which negate the technical, administrative and physical controls already in place.

